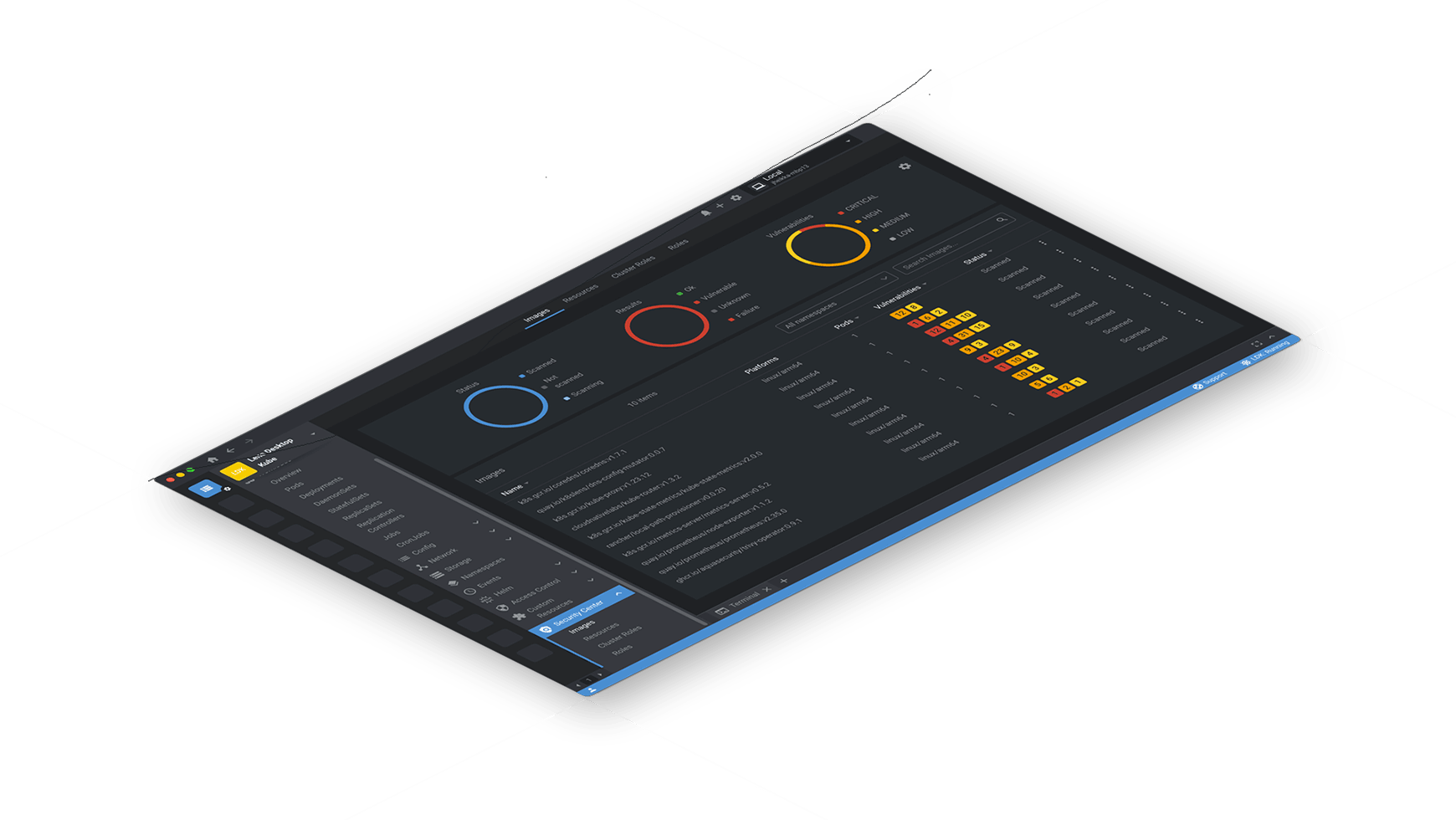
Introducing Lens Security Center
In today’s world, security is of utmost importance for all organizations, and we understand that at Lens. That’s why we’re proud to introduce Lens Security Center, a feature that empowers Lens users to identify vulnerabilities and misconfigurations in their workloads and clusters with ease. The best part? It’s already built-in into Lens Desktop, so there’s no need for additional installations. All you need to do is connect to your cluster and start scanning. Lens Security Center surfaces potential vulnerabilities in images, resources, roles and cluster roles that are immediately relevant and actionable. You can drill down and get more information about any CVEs or misconfigurations that are flagged. You can even set up automatic scanning by deploying an operator to your cluster with a simple toggle switch.
We understand that some organizations may already have a centralized scanning system in place. However, detecting vulnerabilities earlier in the development cycle, before even reaching a CI/CD system, can save you time, money, and reduce risks. With Lens Security Center, you can easily integrate your existing scanning system and see those vulnerabilities directly in Lens. This eliminates the need to jump between multiple dashboards and get overwhelmed by CVEs to find what you’re looking for.
We are excited to offer Lens Security Center as part of our Lens Pro subscription. This feature provides additional layers of security for your workloads and clusters, giving you the peace of mind you need to focus on building great applications.
Lens Security Center
With Lens 6 we introduced Lens Security which provides container image scanning and CVE reporting for everybody using Lens Desktop. Since then we have been hard at work and have expanded upon this feature and turned it into Lens Security Center. Let’s take a closer look!
Images
Images offers powerful container image scanning and CVE reporting capabilities. You can easily browse through the container images running in your cluster, namespace, deployment, or even pod and spot scan images to immediately see their vulnerabilities and correct them before they reach a centralized scanning system. The details of a CVE include its severity, the affected software and potential mitigations. For example, the scanner will surface images that could contain buffer overflows, out-of-bounds, denial of service, command injection, or code execution vulnerabilities.
Resources
Resources provides an immediate way to assess your images, workloads, and infrastructure components against Kubernetes configuration security standards. With Resources, you can quickly and easily check that your Kubernetes environment is configured in accordance with best practices, and identify potential security vulnerabilities before they become a problem. For example, you can verify that a deployment is not running as a root user, or confirm that it has set resource requests and limits. Or validate that sharing the host’s PID namespace does not allow visibility on host processes, potentially leaking information such as environment variables and configuration. These checks can be applied to a variety of Kubernetes workloads and other namespaced resources, including Services and ConfigMaps, providing comprehensive security coverage across your Kubernetes resources.
Roles & Cluster Roles
Lens Security Center offers comprehensive scanning of the roles, cluster roles, access rights, and permissions of critical resources within your Kubernetes cluster. You can quickly and easily verify that your Kubernetes environment is configured to meet your organization’s security requirements. For example, you can check that a given role does not expose permissions to secrets for all groups, which can help prevent unauthorized access to sensitive data. You can see which roles permit specific verbs on wildcard resources. Or you can check whether a role permits update/create of a malicious pod.
Get Social with Avatars
Personalize your Lens experience with your own avatar! Whether you’re inviting new members to a Space, seeing who’s connected to a shared cluster, or discovering members of the Lens community in our forums, your avatar will make you stand out. You can choose a photo of yourself, a character you like, or a custom design. Uploading your avatar is easy and takes only a few seconds.
Support for Additional Kubernetes Kinds
As the Kubernetes API evolves, we strive to have comprehensive coverage and have recently incorporated support for several new Kubernetes Kinds, including Vertical Pod Autoscaler, Ingress Classes, Replication Controllers, and limited support for Sub-namespaces.
Improved Upgrading for Linux
We have improved the upgrade experience for Linux users by offering RPM packages natively built and released via YUM repository, as well as Deb packages released via APT repository.
Local TLS encryption
Lens Desktop has been updated to utilize TLS encryption for local internal communication, further increasing security.
Other Enhancements
- HPAs get loaded using version v2 for newer Kubernetes, and new fields such as behavior and metrics are no longer broken.The versions of HPAs’ uses is now dynamic to the version hosted on the cluster.
- Added a restart button to the menu for StatefulSets.
- Provided a more useful editor with Tab key support for ConfigMap data entries.
- Allowed the use of relative paths within Kubeconfig files. They are relative from the path from which the kubeconfig file has been shared with Lens Desktop.
- Allowed specifying ResourceName in KubeObjectListLayout.
- Clicked actions now benefit from better UX and visibility. New component <NamespaceSelectBadge/> refactored out from multiple resource views with excessive dependencies.
- Added a restart button to the menu for DaemonSets.
- Made AppMenus optionally IComputedValue similar to trayMenus. And extensions dynamically show/hide menu items.
- NamespaceSelectBadge won’t have to be used in all places anymore.
- Allowed extensions’ developers to place ClusterPageMenuRegistrations in places other than at the bottom of the cluster view sidebar.
- Added the ability for KubeApi to filter server versions.
- Computed catalog source is allowed from extension.
- Hierarchical Namespaces are now displayed as a tree within Namespace Details.
- Enabled extensions to specify storeName for persisting data.
- Added bundled extension versions to ‘About Lens’.
- RequestMetrics has been exported to the extension api.
Bug Fixes
- Fixed terminal window paddings.
- Kubeconfig sync is fixed and is now saving data.
- HPA metrics from different versions can be parsed.
- Small TabLayout doesn’t jump anymore when switching pages.
- Fixed a typo and adjusted some grammar for the messaging about dragging and dropping extension packages into the application window.
- Now the hashed directory for the extensions is ensured.
- You can use setCertificateVerifyProc to verify lens proxy certificates.
- Fixed removePath functionality to also include directories.
- Namespace details are now opening.
- The app is not crashing anymore when sometimes using MonacoEditor.
- Fixed the shouldShowResource when the user is not a cluster admin.
- Fixed a regression that caused breaking changes in the Extension API.
- You are now able to add new Kubeconfig syncs.
- Fixed the KubeJsonApi.forCluster that was missing from the extension API and removed class constructors that require dependencies.
- There is no more delay removing iframe to fix renderer crash.
- Fixed KubeJsonApi.forCluster as part of the extension API.
- Error messages are now broadcasted within Cluster.getConnectionStatus.
- Changed the renderer attempting to load CAs to go through main.
- Added more resiliency to listing Kubernetes API resource kinds.
- PodDistruptionBudgets are now displayed on newer Kubernetes versions.
- Enabled the export type-space versions of constructors to fix the extension API.
- Fixed getting metrics’ names for HPA v1.
- Fixed the monaco editor’s scroll block in config map details.
- You can now export more things for the extension API.
- Configured core package dependencies as externals for webpack, cleaned up core webpack configuration, removed unused webpack plugins from core.
- Fixed invalid bin links causing errors on Windows.
- Fixed common extension api bundling.
- You can use setCertificateVerifyProc to verify lens proxy certificates.
- Fixed the typing issue with userStorePreferenceDescriptorsInjectable.
- Fixed the issue keeping the node shell from loading due to Host/certificate mismatch.
- Added a bit of spacing before the Installed extensions title.
- Fixed the extension installation.
- Fixed the issue that made monaco-editor store the value somewhere with the ID and prefer stored value even when the editor is remounted.
- Fixed the external extensions not loading initially.
- Fixed empty pod logs tab content.
- Now the hashed directory for the extensions is ensured.
- Fixed the dropdown items readability in Dock.
- The command line argument is now being passed to lerna.
- Fixed the PodList TableHead overflow.
- @k8slens/extensions is no longer broken after monorepo.
- Bumping up version numbers for a big number of internal components and dependencies.
About Lens
Lens is the way the world runs Kubernetes. It’s lowering the barrier of entry for people just getting started and radically improving productivity for people with more experience. Users of Lens gain clarity on how their clusters and cloud native software stacks work. It helps people to put things in perspective and to make sense of it all.
Tens-of-thousands of businesses and hundreds of thousands of users develop and operate their cloud native workloads on Lens. It is built on open source, has 20.6k stars on GitHub, and is backed by a number of Kubernetes and cloud-native ecosystem pioneers. Lens is the largest and most advanced Kubernetes platform in the world.